Overview
Our Certified Ethical Hacker (CEH) certification training course offers you a comprehensive grasp of ethical hacking stages, diverse attack paths, and preventive measures. Delve into the mindset and tactics of hackers, empowering you to fortify your security setup and thwart potential attacks. By understanding system weaknesses and vulnerabilities, you will help organisations strengthen their security protocols and decrease the risk of incidents. Our funded CEH training course is designed to integrate practical experience and a structured approach across all ethical hacking domains and methodologies.
This certification offers you the opportunity to demonstrate essential knowledge and abilities necessary for the role of a certified ethical hacker in Singapore. Through this journey, you will adopt a new mindset regarding the obligations and strategies necessary for ensuring security.
Course Description & Learning Outcomes
In its 11th version, CEH continues to evolve, adapting to the newest operating systems,
exploits, tools, technologies and strategies. Here are some significant enhancements introduced in CEH v11.
- Incorporating Parrot Security OS
- Re-Mapped to NIST/NICE Framework
- Enhanced Cloud Security, IoT, and OT Modules
- Modern Malware Analysis
- Covering the Latest Threats – Fileless Malware
- New Lab Designs and Operating Systems
- Increased Lab Time and Hands−on Focus
- Industry’s Most Comprehensive Tools Library
What You Will Learn ?
- Key issues plaguing the information security world include ethical hacking, information security controls, laws, and standards.
- Conduct foot printing and reconnaissance utilising cutting-edge techniques and tools as an essential pre-attack phase required in ethical hacking.
- Network scanning countermeasures and techniques.
- Enumeration countermeasures and techniques.
- Conducting vulnerability analysis, which involved identifying security weaknesses within the network, communication infrastructure, and end systems of the target organization.
- Unveiling system and network weaknesses using techniques such as steganalysis attacks, system hacking methodology, covering traced and steganography.
- Social engineering techniques and how to identify theft attacks to audit human- level vulnerabilities and suggest social engineering countermeasures.
- DoS/DDoS tools and attack techniques to audit a target and DoS/DDoS countermeasures.
- Various forms of malware (such as Trojans, viruses, worms, etc.), conducting system audits to detect malware attacks, analysing malware, and implementing countermeasures.
- Countermeasures, session hijacking techniques to uncover session management at network-level, authentication/authorisation, and cryptographic weaknesses.
- Packet sniffing techniques to discover network vulnerabilities and countermeasures to defend sniffing.
- Assessing vulnerabilities in web applications involves utilizing a comprehensive web application hacking methodology to identify web application attacks and implementing appropriate countermeasures.
- Countermeasures, injection detection tools to detect SQL injection attempts, and SQL injection attack techniques.
- Web server attacks and a comprehensive attack methodology to audit vulnerabilities in web server infrastructure, and countermeasures.
- IDS, honeypot and firewall evasion techniques, evasion tools and techniques to audit a network perimeter for weaknesses, and countermeasures.
- Attack vectors on mobile platforms, exploits targeting Android vulnerabilities, and guidelines along with tools for enhancing mobile security.
- Discover potential risks targeting IoT and OT platforms and acquire strategies for securely safeguarding IoT and OT devices.
- Wireless encryption, wireless hacking tools, wireless hacking methodology, and Wi-Fi security tools.
- Penetration testing, security audit, vulnerability assessment, and penetration testing roadmap.
- Public Key Infrastructure (PKI), cryptography ciphers, cryptanalysis tools, and cryptography attacks.
- Cloud computing concepts (Server less computing, container technology), various threats/attacks, and security techniques and tools.
Course Outline
- Introduction to Ethical Hacking
- Reconnaissance and Foot printing
- Scanning Networks Enumeration
- Vulnerability Analysis
- Malware Threats
- System Hacking
- Session Hijacking
- Honeypots, firewalls and IDS
- SQL Injection
- Hacking Wireless Networks
- Hacking Web Applications
- Hacking Mobile Platforms
- Hacking Web Servers
- Sniffing
- IoT Hacking
- Cloud Computing
- Social Engineering Denial-of-Service
- Cryptography
The objective of this funded CEH course is to assist you in becoming a master of ethical hacking methodology that can be used in an ethical hacking or penetration testing situation. Our expert-led, funded programs can elevate your cybersecurity journey. With online flexibility and comprehensive content, become a certified ethical hacker ready for any penetration testing scenario, all through our convenient online training courses.
At the end of this course, you will be prepared for EC-Council Certified Ethical Hacker exam 312-50.
For more information, please click here.
Recommended Prerequisites
No prerequisites required for this course.
Who should attend?
- System Administrators
- Network Administrators and Engineers
- Web Managers
- Auditors
- Ethical Hackers
- Security Professionals in General.
Schedule
End Date: 08 Nov 2024, Friday
Start Date: 4 Nov 2024, Monday End Date: 8 Nov 2024, Friday Duration: 5 Days, 36.25 hours Timing: 9am - 5.15pm Location: Virtual
Location: OnlinePricing
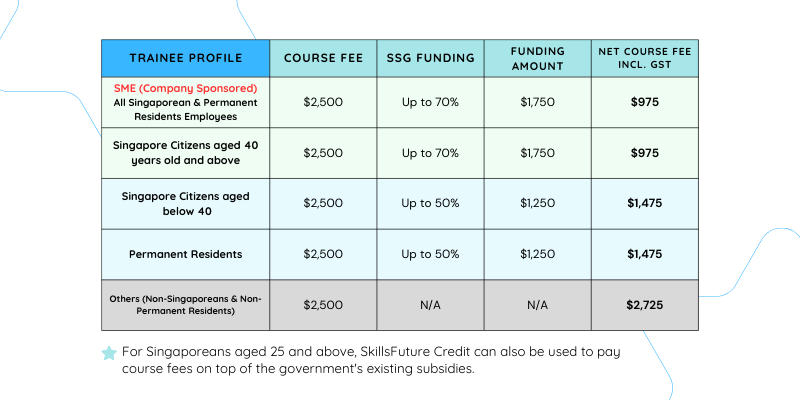
Course fees: If you meet the eligibility criteria, course fees can be subsidised by up to 70%. Moreover, SkillsFuture Credit can be applied to cover course fees in addition to existing government subsidies.