Overview
If you are seeking to establish yourself as a reputable information security professional, the Certified Information Systems Security Professional (CISSP) certification is widely recognised in Singapore and internationally. Engaging in CISSP online training can validate your managerial and technical expertise, demonstrating your capability to effectively engineer, design, and oversee an organisation's security framework. The CISSP Common Body of Knowledge (CBK) covers a comprehensive range of topics, ensuring its relevance and applicability across various domains within the information security field.
At the end of this course, you will be able to gain comprehensive and up-to-date knowledge that aligns with the certification requirements of (ISC)² (International Information System Security Certification Consortium, Inc.), renowned as the gold standard for security professionals. This certification is essential for a career in security-related roles, equipping you with the skills necessary to safeguard your organization against sophisticated cyber-attacks. You will also develop a solid background in security concerns, communications, infrastructure, basic cryptography, and operations, along with hands-on experience to effectively design, implement, and manage a security program.
Course Description & Learning Outcomes
Course Outline
The 5-day course heavily focuses on the eight fundamental domains of Information Security.
Domain 1: Risk and Security Management
1.1 Understand and apply concepts of integrity, confidentiality and availability
1.2 Assess and apply security governance principles
1.3 Establish compliance requirements
1.4 Understand regulatory and legal issues that concern information security in a global context
1.5 Understand, promote, and adhere to professional ethics
1.6 Develop, document, and implement security policy, procedures, standards and guidelines
1.7 Analyse, identify and prioritise Business Continuity (BC) requirements
1.8 Enforce and contribute to personnel security guidelines and procedures
1.9 Apply and understand risk management concepts
1.10 Apply and understand threat modelling methodologies and concepts
1.11 Implement risk-based management concepts in the supply chain
1.12 Maintain and establish a security education, awareness and training program
Domain 2: Asset Security
2.1 Identify and classify assets and information
2.2 Determine and maintain asset ownership and information
2.3 Protect privacy
2.4 Ensure proper asset retention
2.5 Determine data security controls
2.6 Establish information and asset handling requirements
Domain 3: Security Architecture and Engineering
3.1 Manage and Implement engineering processes using secure design principles
3.2 Recognise the basic concepts of security models
3.3 Select controls based on systems security requirements
3.4 Recognise security capabilities of information systems (e.g., encryption/decryption, memory protection, Trusted Platform Module (TPM),
3.5 Mitigate and assess the vulnerabilities of security architectures, solution elements and designs
3.6 Mitigate and assess weaknesses in web-based systems
3.7 Mitigate and assess weaknesses in mobile systems
3.8 Mitigate and assess weaknesses in embedded devices
3.9 Apply cryptography
3.10 Apply security principles to facility and site design
3.11 Implement facility and site security controls
Domain 4: Communication and Network Security
4.1 Apply secure design concepts in network architectures
4.2 Secure network components
4.3 Apply secure communication channels according to design
Domain 5: Identity and Access Management (IAM)
5.1 Control logical and physical access to assets
5.2 Manage authentication and identification of people, devices, and service
5.3 Integrate identity as a third-party service
5.4 Manage and implement authorisation mechanisms
5.5 Manage the identity and access provisioning lifecycle
Domain 6: Security Assessment and Testing
6.1 Design and verify tests, assessments and audit strategies
6.2 Manage security control testing
6.3 Manage security process data (e.g., technical and administrative)
6.4 Examine test output and generate a report
6.5 Manage or facilitate security audits
Domain 7: Security Operations
7.1 Support and understand investigations
7.2 Understand requirements for investigation types
7.3 Conduct monitoring and logging activities
7.4 Securely provisioning resources
7.5 Apply and understand foundational security operations concepts
7.6 Apply resource protection techniques
7.7 Conduct incident management
7.8 Maintain and operate detective and preventive measures
7.9 Support and implement patch and vulnerability management
7.10 Understand and Engage in change management processes
7.11 Apply recovery strategies
7.12 Apply Disaster Recovery (DR) processes
7.13 Test Disaster Recovery Plans (DRP)
7.14 Participate in Business Continuity (BC) exercises and planning
7.15 Manage and implement physical security
7.16 Address security concerns and personnel safety
Domain 8: Software Development Security
8.1 Understand and incorporate security in the Software Development Life Cycle (SDLC)
8.2 Recognise and apply security controls in development environments
8.3 Evaluate the benefits of software security
8.4 Evaluate the security impact of acquired software
8.5 Define and implement secure coding standards and guidelines
For more information, please click here.
Recommended Prerequisites
You must either have:
- a prior full-time work experience of at least five years in 2 or more of the eight domains listed above
- or hold a 4-year college degree equivalent.
Who should attend?
This training course is targetted toward those who are experienced information security professionals in Singapore who wish to gain an internationally recognised accreditation while expanding their knowledge, including:
- IT Consultants
- Information Security Officers
- Network Administrators
- Security Consultants
- Security Device administrators
- Security Engineers
- Security Managers
- Security Policy writers
- Privacy Officers
Schedule
End Date: 22 Nov 2024, Friday
Start Date: 18 November 2024, Monday End Date: 22 November 2024, Friday Duration: 5 Days, 35 hours Timing: 9am - 5pm Location: Virtual
Location: OnlinePricing
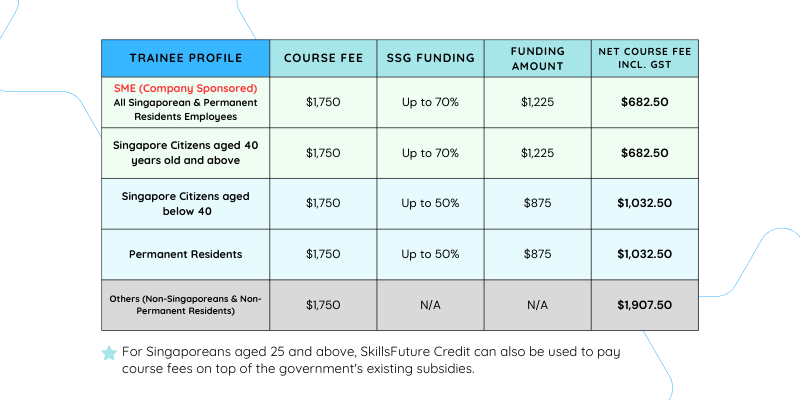
Course fees: If you meet the eligibility criteria, course fees can be subsidised by up to 70%. Moreover, SkillsFuture Credit can be applied to cover course fees in addition to existing government subsidies.